What We Protect
Exploring the problems
Automotive
At the Black Hat conference in Las Vegas in 2015, researchers infiltrated the networks of newer cars to gain control of their steering, radio and automated driving features.
 Source: wired.com
Source: wired.com
Consumer Electronics
Hackers used malware to capture nude pictures of Miss Teen USA using her webcam.
 Source: tnw.com
Source: tnw.com
Data Security
A data hack on government servers resulted in the theft of personal information, including Social Security numbers, of roughly 21.5 million people.
 Source: cnn.com
Source: cnn.com
Power & Utilities
79 hacking incidents on energy companies were investigated by the Department of Homeland Securityin 2014 and recent survey results show that more than 37% of energy companies are vulnerable to security breaches.
 Source: money.cnn.com
Source: money.cnn.com
Industrial
Hackers sneaked malware into computers at power plants, energy grid operators, gas pipeline companies and industrial equipment makers.
 Source: money.cnn.com
Source: money.cnn.com
Overwatch ThreatWatch™
See threats. Take action.
ThreatWatch™ is Overwatch's real-time threat assessment and algorithmically based monitoring tool, which warns users of security risks as they occur.
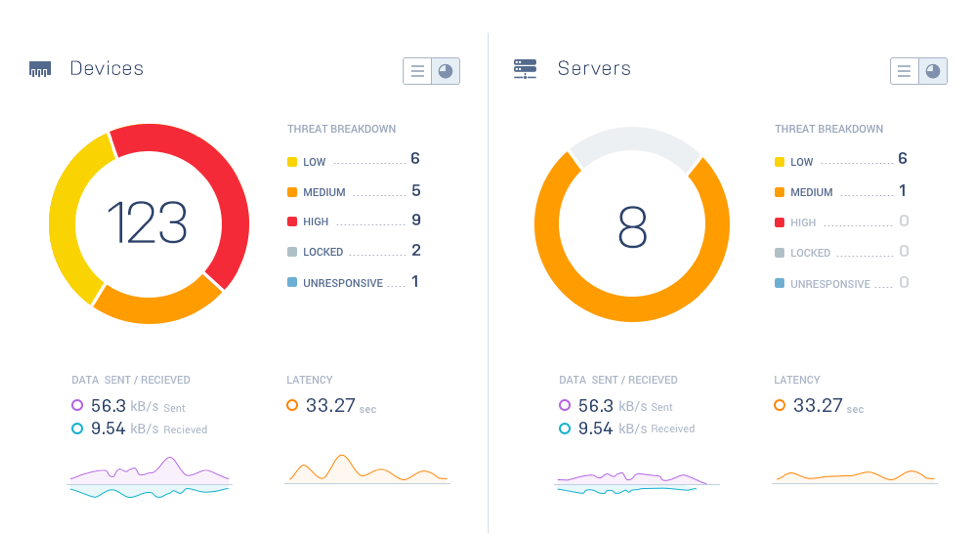
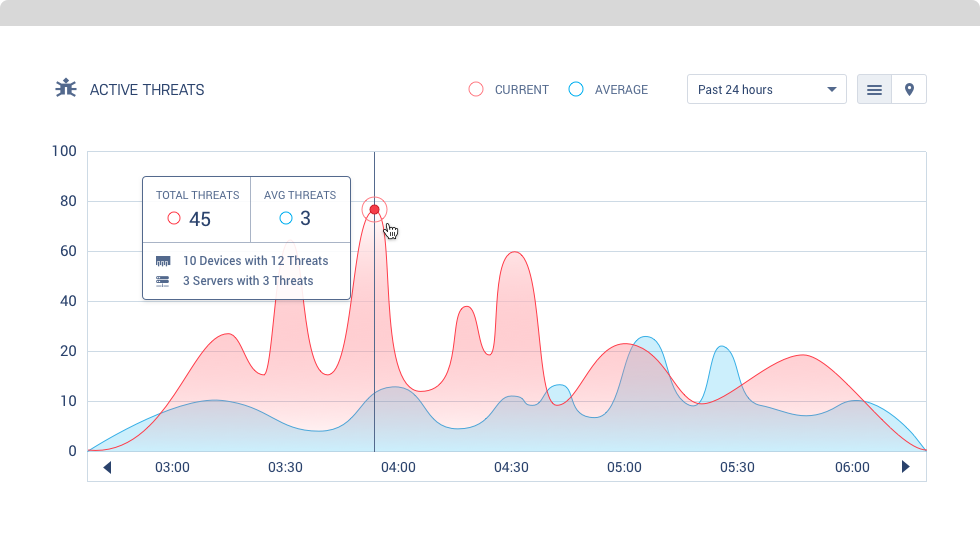
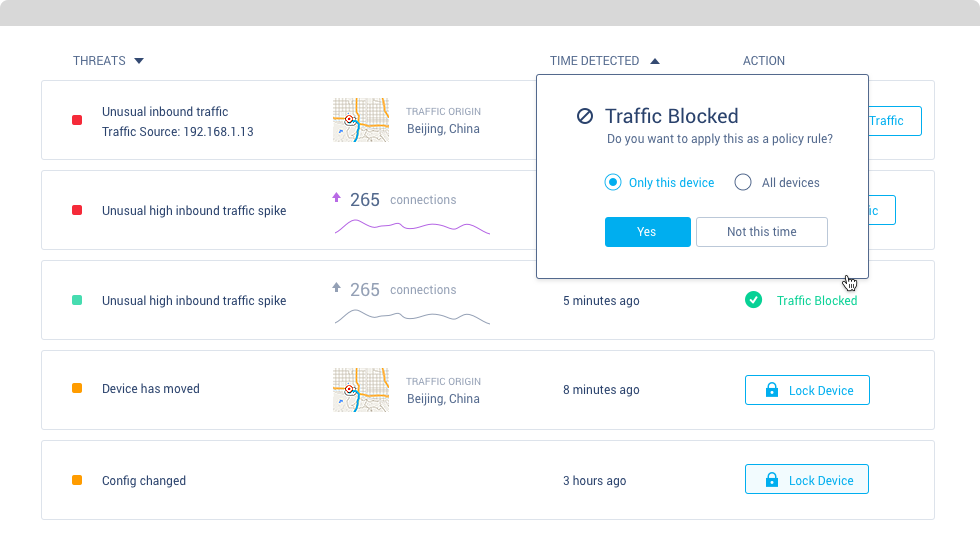
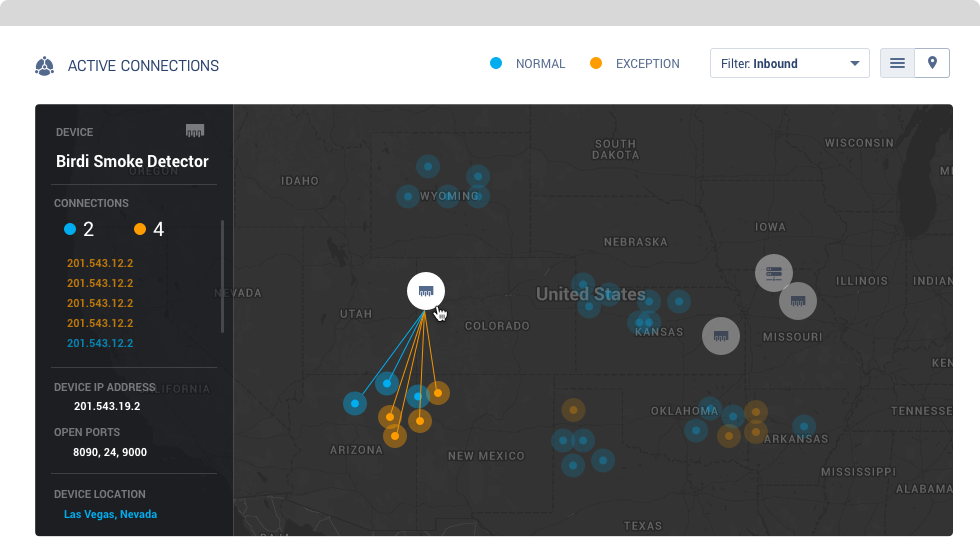
How Overwatch Works
Software defined security.
Your devices run the Overwatch Client Agent, a Powerful lightweight device Agent built to withstand intrusion. These report intelligence to our server-side gateway, which also communicates with the Agents to provide real-time threat assessment and mitigation.
The Agent and our API are in constant communication with our user facing Security Application, which provides tools to manage device security, threat alerting, and insights, using our patent pending ThreatWatch™ algorithms.

